Introduction
“You can’t protect what you can’t see.” This truth defines modern IT security. Unmanaged devices—from rogue IoT gadgets to forgotten laptops—create silent risks across networks. Studies show 92% of ransomware attacks in 2024 began with such untracked assets, revealing a clear visibility gap. With hardware asset management (HAM), IT gains real-time control, enabling Zero Trust enforcement and proactive defense before vulnerabilities are exploited.
To explore detailed strategies, tools, and best practices, check out our comprehensive guide to Hardware Asset Management — a must-read for IT and finance teams aiming to optimize visibility and control.
In this post, we’ll explore how effective HAM boosts cybersecurity. Specifically, we’ll see how HAM reduces the risk of untracked devices causing breaches. We’ll also cover how it enables Zero Trust strategies, helps meet compliance requirements, and even controls IT costs.
Hardware asset management isn’t just an IT chore. It’s a strategic IT security investment for leaders across IT, Finance, and Digital Transformation.
The Hidden Risk of Untracked Devices (untracked devices security risk)
Shadow IT and untracked devices are invisible vulnerabilities. When IT lacks visibility into every device on the network, those “shadow” assets become ticking time bombs. Unmanaged hardware often misses critical patches or security controls, and attackers actively hunt these weak links. Untracked devices fly under the radar, making them a major security risk:
-
Easy targets for attackers:
Unmanaged devices often run outdated software or use default passwords, so they harbor known vulnerabilities. These weaknesses make them perfect entry points for malware and hackers.
-
Blind spots in audits:
If a device isn’t tracked in the asset inventory, it won’t show up in security audits or compliance checks. Nearly 46% of enterprises have faced audit delays due to incomplete hardware records.
Attackers thrive on exploiting blind spots in enterprise networks. In one case, hackers breached a casino’s system through an IoT thermostat in a fish tank, using it as an open backdoor. Such untracked devices often lack proper security, making them easy targets. Even ordinary gadgets can trigger massive breaches when IT teams don’t know they exist.
Can maintaining a complete device inventory prevent breaches? Absolutely. A real-time hardware inventory helps IT teams identify, secure, and update every device—from laptops to IoT endpoints. This proactive control eliminates blind spots that hackers often exploit. In essence, hardware asset management (HAM) ensures nothing goes unseen, strengthening your organization’s overall security posture.
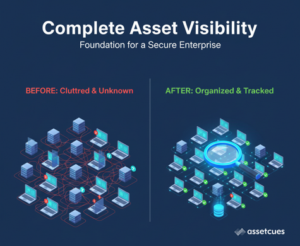
Complete Asset Visibility as a Security Foundation (IT asset visibility security)
Security teams can’t protect what they can’t see. Hardware asset management (HAM) delivers full asset visibility, creating a single source of truth for every device. With details like owner, location, and configuration, IT gains precise control. This clarity strengthens defenses and ensures a resilient security posture.
With a unified hardware inventory (think “visibility = control”), IT knows exactly what devices exist in the organization. If a device exists, it’s on your radar—no more guessing or surprises. Full visibility enables proactive security measures rather than reactive firefighting.
Full visibility helps IT teams quickly detect vulnerabilities and compliance gaps. HAM tracks each device’s OS, firmware, and patch level to spot missing updates. It also flags unauthorized or rogue devices, allowing IT to remove shadow IT risks swiftly.
This live inventory enables a proactive security posture. IT can automate patch deployment across all known devices, and enforce security policies (encryption, strong passwords, MFA, etc.) uniformly on every endpoint. Teams can plan timely replacements of legacy hardware before those devices become security liabilities.
This vigilance is essential for preventing breaches. A Trend Micro study found that 74% of cybersecurity leaders faced incidents from unknown or unmanaged assets. In short, most breaches start with devices outside IT’s visibility. By tracking every asset, HAM eliminates these blind spots and greatly reduces security risks.
Importantly, visibility isn’t just an IT concern. It also reassures Finance by protecting asset value and avoiding redundant purchases, and it keeps Risk/Compliance teams happy by maintaining an audit-proof record of all assets. In short, hardware asset visibility turns chaos into control. It’s a foundational pillar of both security and operational efficiency.
Enforcing Zero Trust with Hardware Asset Management (asset management zero trust)
Modern cybersecurity is embracing the Zero Trust model of “never trust, always verify.” A core pillar of Zero Trust is Device Trust—ensuring any device accessing your network is known, secure, and continuously verified. This is exactly where hardware asset management shines. You simply cannot implement Zero Trust without a complete inventory of all your devices.
Under the Zero Trust model, every user and device must prove trust before access. As the framework states, “Zero Trust requires full awareness of all network devices.” Without an updated asset inventory, IT can’t verify a device’s identity or security status. Therefore, any untracked device should be denied access under Zero Trust principles.
HAM makes device trust achievable by integrating rich asset data into your security controls:
-
Policy enforcement:
Unknown devices (not found in the inventory) can be automatically blocked from the corporate network—no trust granted by default. If a known device falls out of compliance (for example, missing critical patches), its access can be limited or even quarantined. It cannot regain normal access until it meets security requirements. Only managed, compliant devices are allowed full access.
-
Continuous monitoring:
HAM also ties into tools like Network Access Control (NAC), mobile device management (MDM), and SIEM systems to monitor device status in real time. If a device deviates from policy (e.g. becomes jailbroken or out of date), IT gets an immediate alert. The security team can then quickly isolate or remediate that device in line with Zero Trust policies.
Read more about the hardware asset management lifecycle
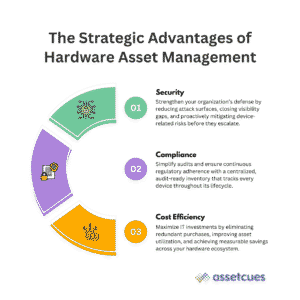
Beyond Security: Compliance and Cost Benefits of HAM 📊
Effective hardware asset management doesn’t just improve cybersecurity – it also strengthens regulatory compliance and optimizes IT costs. This unified approach appeals across the C-suite, from CIOs and CISOs to CFOs and digital transformation leaders looking at the bigger picture.
-
Regulatory Compliance & Audit Readiness:
HAM enhances regulatory compliance by maintaining an audit-ready hardware inventory that simplifies inspections. It enforces device policies, ensuring only approved, secure devices access sensitive data. HAM also tracks assets through end-of-life disposal, confirming proper data wiping or destruction. Together, these controls prevent compliance gaps and strengthen overall audit readiness.
-
IT Cost Control & Efficiency:
A strong HAM program quickly delivers cost savings and better asset utilization. With full visibility, IT avoids duplicate purchases and unused hardware sitting idle. Studies show 20–30% of IT budgets go to underused devices, but HAM cuts this waste effectively. By reallocating idle assets—like assigning an unused laptop to a new hire—organizations can reduce operational costs by 8–15% per asset.
Explore how hardware asset management drives cost savings >>
Asset tracking helps IT teams optimize maintenance and upgrades efficiently. HAM logs each device’s warranty, support contract, and lifecycle stage, guiding timely actions. This ensures repairs or replacements happen neither too early nor too late, maximizing value. As a result, organizations use warranties fully, avoid unexpected failures, and reduce unplanned expenses.
Expert insight: One IT director who overhauled his company’s asset tracking noted, “Implementing a robust hardware asset management program not only tightened our security, but also reduced our annual IT asset costs by 20% and simplified our compliance audits.” This kind of firsthand result underscores that HAM isn’t just about inventory – it’s about running a more secure, efficient, and audit-ready organization.
FAQ (Frequently Asked Questions)
Q1: How does hardware asset management improve security?
A: It gives IT complete visibility and control over every device, so nothing slips through the cracks. By tracking all hardware, HAM ensures devices get timely patches, unauthorized devices are spotted and removed, and security policies (like encryption or MFA) are enforced everywhere. In short, HAM closes the security gaps that unmanaged devices would open.
Q2. What are the 5 pillars of IT security?
A. The five pillars of IT security are confidentiality, integrity, availability, authentication, and non-repudiation. Together, they ensure data protection, system reliability, and secure user access.
Conclusion & Call to Action
In summary, hardware asset management (HAM) is far more than IT housekeeping—it’s a strategic security investment. By revealing every device, HAM reduces risks, supports Zero Trust, and simplifies compliance. It also cuts costs by improving asset utilization and preventing waste. Ultimately, HAM builds a secure, efficient, and audit-ready organization, giving IT confidence that no device remains unseen.
Ready to close your IT visibility gap? Embrace a unified hardware asset management (HAM) approach to protect both your enterprise and bottom line. Strengthening visibility enhances security, streamlines compliance, and optimizes costs across your infrastructure. To see these benefits firsthand, schedule a personalized demo with our team today—because proactive asset management builds a safer, smarter enterprise for tomorrow.